
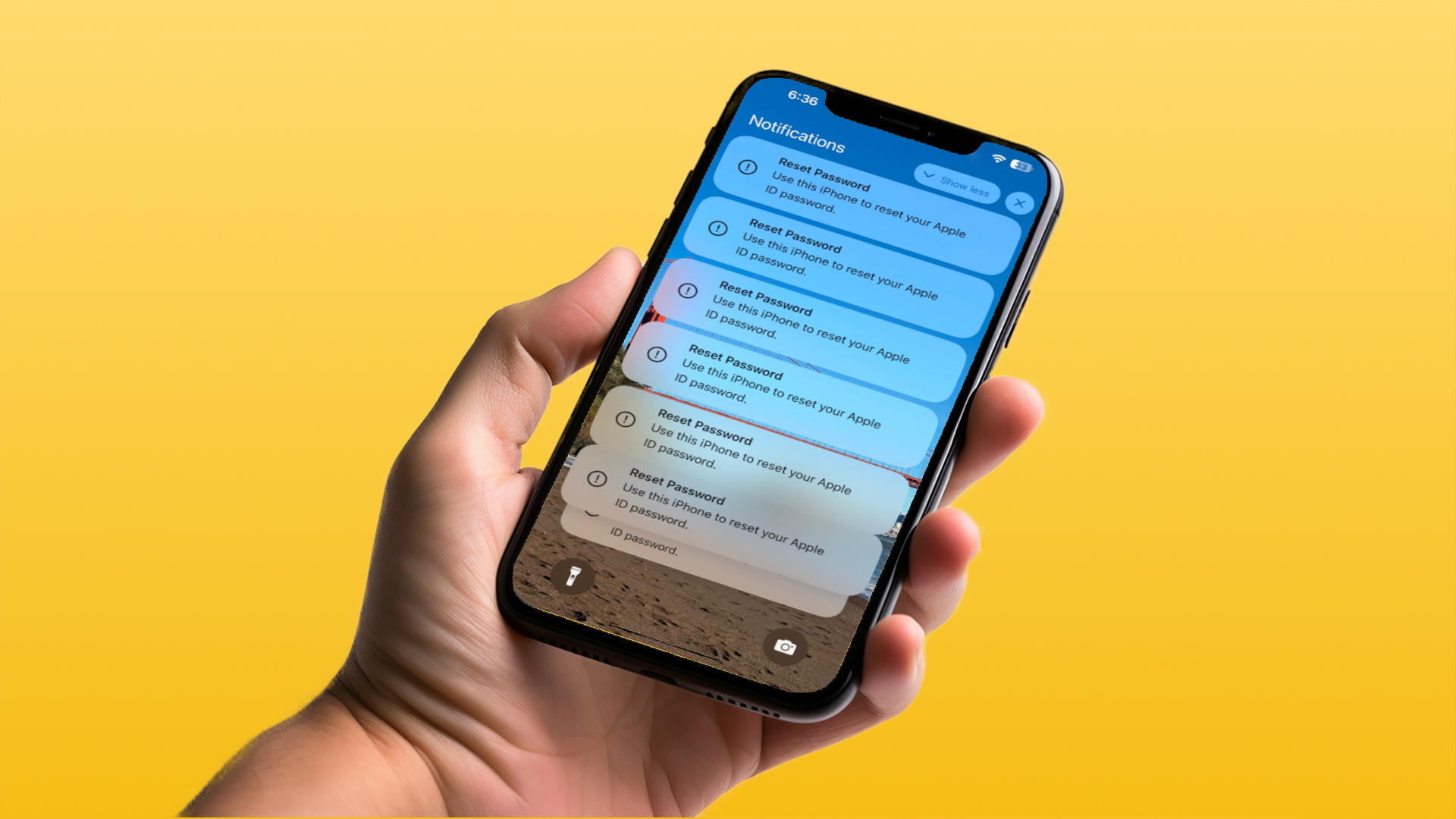
Phishing attacks are on the rise, with these nefarious security threats breaching your accounts, stealing your credit information, or accessing your private files. Scams like these see you simultaneously play the part of an active (yet unwitting) co-conspirator in attempts to hijack your most sensitive data.Far beyond the simplistic and often easy-to-spot cold-calling techniques of supposed Microsoft Tech support agents or Amazon customer service employees, a new phishing threat has arisen whereby iPhone users are being targeted by the misuse of Multi-Factor Authentication (MFA) in efforts to trick them into handing over complete control of their Apple account.Unlike other phishing attacks that might require a user to divulge passwords, personal details, or banking information, all this attack requires to successfully rob you of your Apple account (and all of the information and banking details linked to it) is a simple tap on the wrong notification.Gone phishing: How ‘Push Bombing’ and ‘MFA’ fatigue attacks target iPhone usersThis kind of phishing is known as “Push bombing” or “MFA fatigue,” a method that continually harasses victims with a stream of notifications that are otherwise (ironically) used to protect people from this exact kind of attack.As reported by KrebsOnSecurity, a bug (or potential oversight) in Apple’s password reset feature has seen cyber-criminals spam their victims with password reset request notifications that force users to tap “Allow” or “Don’t Allow” before proceeding.While it’s easy enough for users to tap “Don’t Allow,” attempting to clear out hundreds of these messages before regaining access to your phone can result in the fatigue part of MFA fatigue, whereby a user might absentmindedly select the wrong option or simply hit “Allow” just to be done with them.The risk of users doing so is all the more likely when the notification in question merely asks if you’d like to “Use this iPhone to reset your Apple ID password” — a weak and vague form of phrasing that could lead some to believe that they are accepting the option to control their passwords only from this device.Get our in-depth reviews, helpful tips, great deals, and the biggest news stories delivered to your inbox.But hitting “Allow” will grant the phishing hopefuls control of your password, leaving you in the dark about how to sign in to your own account once they complete the reset. Leaving users targeted by this form of attack helpless but to continually and carefully choose “Don’t Allow” each time. However, even after that, the risk persists.(Image credit: Laptop Mag / Sean Riley)If at first you don’t succeed…A second stage of the attack is then likely to follow, whereby the scammers then call their target, spoofing the Apple Support phone number in the process, to inform them that there is a fault or a third-party attack in process and that Apple Support needs to verify a one-time code in order to resolve it.Of course, Apple Support is not prone to making outbound calls to customers unless it is specifically requested, and that one-time code that’s requested of you would give the attackers the 2FA (Two-factor authentication) blessing to change your password and lock you out of your account.(Image credit: Laptop Mag/Sean Riley)How to prevent phishing attacks against your Apple accountSadly, protecting yourself from this form of attack can’t be prevented by ticking a checkbox or enabling a setting somewhere on your device. It’s up to Apple to implement some form of measure that impedes an attacker’s ability to disrupt its users in this way.Until then, you’ll have to rely on your own vigilance when it comes to avoiding being duped by ne’er-do-wells seeking to abuse this security feature in their attempts to catch you off-guard.Always stay alert to the kind of notifications you’re receiving, especially when it has anything to do with passwords or device permission. And, as with any type of cold-calling, you should never divulge personal information over the phone — no matter how a person identifies themselves to you and no matter how much accurate information they have to hand about you in their attempts to verify themselves.If you’re ever asked to share a one-time code, click a link in a dodgy-looking email, or hand over personal information in any way over the phone (or through email) then break the line of contact and reach out to that company directly. This ensures that you know with 100% certainty that who you are speaking to is actually whom they claim to be.More from Laptop Mag





